CCTV Policy
Last updated August 28, 2024
POLICY STATEMENT
CloudConsole, the CloudConsole, requires that all information technology (IT) devices be configured such that they can be managed and secured to maintain confidentiality, integrity and availability of research, and business resources and to enable IT configuration standards to meet certain industry, and regulatory requirements. Information technology that inputs, transmits, processes, or stores data must be configured in accordance with the applicable configuration standard. Standards must be written and maintained by the unit responsible for the management of the technology in cooperation with Cybersecurity. Prior to implementation, IT configuration standards must meet the applicable configuration standard to protect data and information technology by ensuring a consistent, secure configuration across technology devices.
STAKEHOLDERS
Stakeholders include directors, officials, managers, employees from both the CloudConsole and the Clients, including end users.
DEFINITIONS
Information Technology Device: Any institutionally or personally owned device to include, desktops, laptops, servers, network/telecommunications equipment, mobile devices, and storage systems that store, process, or transmit Augusta University data.
CloudConsole: Entity or unit owning responsibility for maintaining or managing information assets and devices as assigned by the Management.
Configuration Standard: A document or collection of documents that describe how a device should be configured. Standards are the specifications that contain measurable, mandatory rules to be applied to a process, technology, and/or action in support of a policy.
Information assets can be defined as:
- All categories of automated information, including, but not limited to, records, files, and data bases; and,
- Information technology facilities, equipment (including endpoints, personal computer systems), and software owned or leased by an organization.
Cybersecurity: Organization’s official responsible for: 1) maintaining the cybersecurity of different types of information within the organization that typically involves maintaining computer networks to ensure that sensitive financial or private information is kept secure and cannot be accessed by someone not authorized to do so; 2) that usually reports to a chief information security officer or other member of upper management, such as a director in charge of information technology (IT) or cybersecurity.
POLICIES
1. Legitimate Purpose
The Closed-Circuit Television (CCTV) systems installed by CloudConsole are used to enhance the safety and security of the company's physical assets, personnel, and visitors. The legitimate purposes include, but are not limited to, deterring and preventing crime, facilitating the identification and prosecution of offenders, monitoring security breaches, ensuring adherence to health and safety policies, and evaluating employee conduct.
2. Lawful Basis for Processing
The processing of personal data through the CCTV system is based on the lawful basis of legitimate interests pursued by CloudConsole, which are the prevention and detection of crime and the enhancement of safety and security. The use of the CCTV system is necessary for these interests and is conducted in a proportionate manner, respecting the privacy rights of individuals.
3. Privacy Impact Assessments (PIAs)
CloudConsole will conduct regular Privacy Impact Assessments to evaluate the impact of the CCTV system on individual privacy and to comply with data protection regulations. These assessments will be reviewed annually or whenever there is a significant change to the CCTV system or its use.
4. CCTV Notice and Placement
Notices informing about the presence of CCTV surveillance will be displayed prominently at all entrances and in areas covered by the CCTV system. The notices will include the purpose of surveillance and contact information for individuals wishing to discuss the CCTV system.
5. Operational Details
Procurement
All CCTV equipment will be procured through approved vendors in accordance with company procurement policies. Device must have a regulatory compliance sheet available: https://dl.ui.com/compliance/UVC-G5-Dome_DoC.pdf
Installation, Operation and Security Control
The CCTV system provides coverage over the following areas:
- Main Work Area
- Storage Area
The cameras operate full-time (24 hours a day, 7 days a week).
One (1) type of CCTV camera is used for all areas with the capacity to zoom in of upto 800% but does not follow or detect individuals.
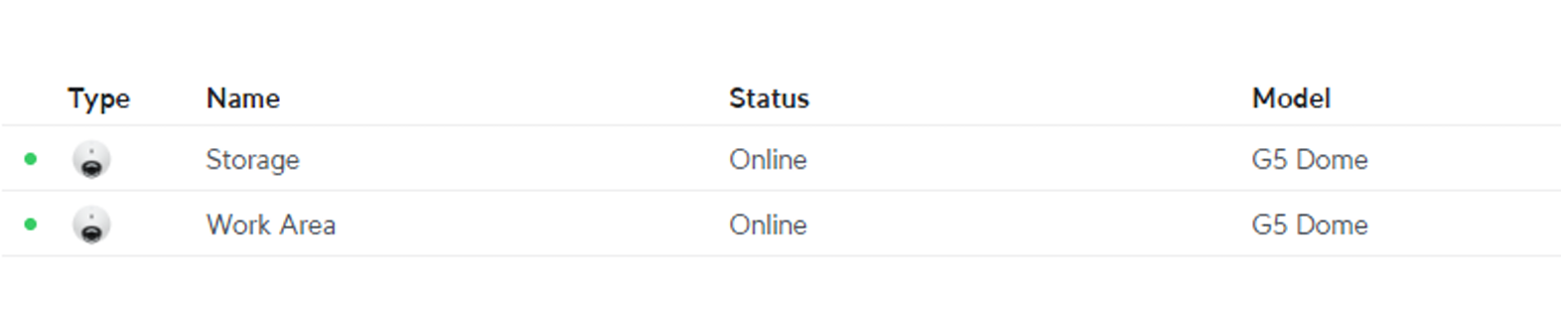

The cameras record movement in the area specific including date, time and location of the footage. It can store upto 18d 5h 42m worth of footage.
The cameras do not conduct sound recording.
The placement of the CCTV cameras shall not unreasonably intrude on the privacy of individuals.
The CCTV system will be controlled centrally by the Security Group under the management of the IT Director.
Monitoring and Maintenance
The monitoring of live feed will be conducted by authorized personnel only. Regular maintenance checks will be conducted to ensure operational integrity. Logs are generated inside the built-in Unifi dashboard and it sends real-time the alerts for any anomalies.
Incident Response and Reporting
CloudConsole abides by the ITIL Service Desk Process.
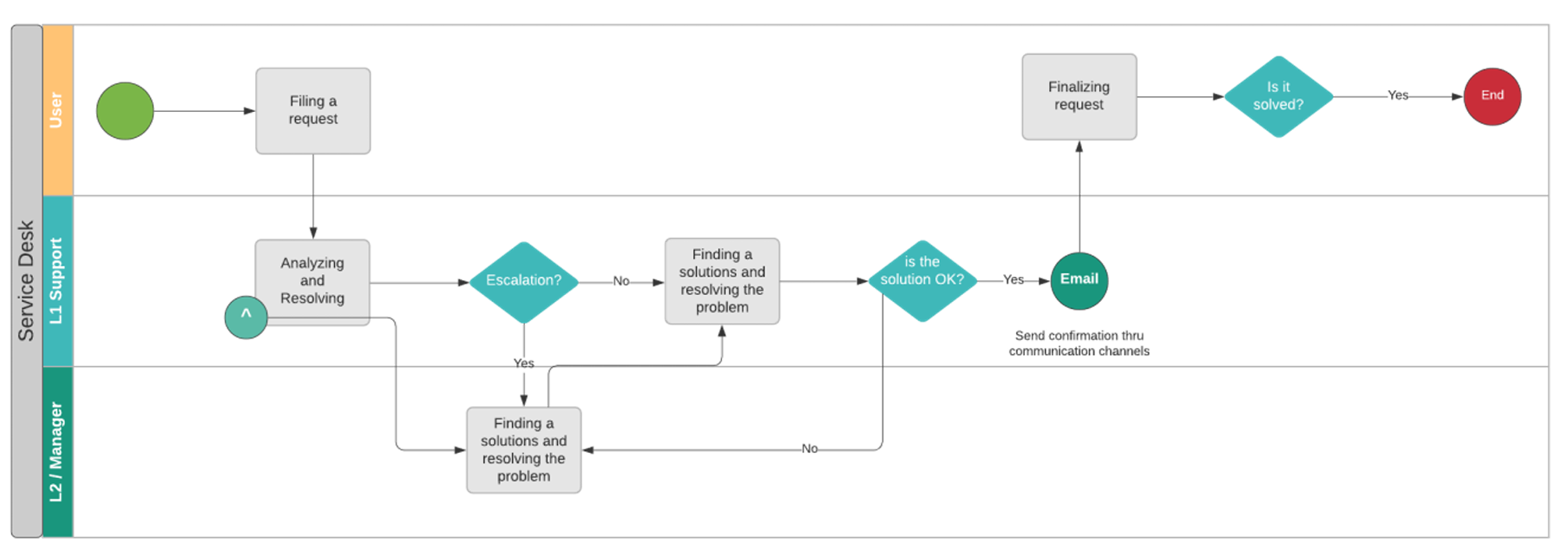

- User: The person who calls the related IT service.
- Support Level 1: This is for basic and simple solutions and is the first point of contact with the user.
- Support Level 2: An analyst specializing in IT that should keep an up-to-date knowledge base for any query from the first level. This is the person who solves cases with the highest level of complexity. (Not included in the current proposal due to changes in the Technical Specification.)
- Manager: A people manager with IT project management skills responsible for coordinating with verticals or teams that require attention to the issue at hand. The people manager also assesses and manages the capability of the service desk personnel to ensure all efforts have been exerted before it is escalated, if no resolution has been met.
Process Workflow
- The user reports a problem and brings all the necessary information so that the Level 1 technician can best direct the call.
- The first level technician analyzes all information submitted by the user and searches the knowledge base for the best solution to the problem.
- If they cannot resolve the issue, the first level technical requests help from the manager / second-level analyst.
- The manager / second-level analyst studies the request and returns the solution. If they find it necessary, the solution is documented in the knowledge base so that the next similar occurrence the first level can resolve the issue without contacting the second level.
- Technical Level 1 confirms the user’s problem will be solved with this solution. If not resolved, returns to the manager / level 2 analyst. If so, the level 1 sends a confirmation to the user.
- The user makes a test solution and checks if it works. If it is not suitable, it is escalated to the Manager, which takes over the process. Manager should escalate to Service Manager if the issue is beyond the accessible systems of the team or if it’s an incident that requires upper management approval. If it is suitable, the process ends.
- The goal is to achieve, over time, fewer calls are sent to the second level. It’s because the knowledge that the manager/level 2 analyst accumulates to develop more complex solutions is always referred to by level 1 and kept in a knowledge base, for easy reference.
- It eliminates an escalation of process flow towards the second level, bringing more agility, and enables the first-level help desk technicians in direct contact with the user.
CloudConsole is expected to follow the steps below when issues or incidents are raised by user.
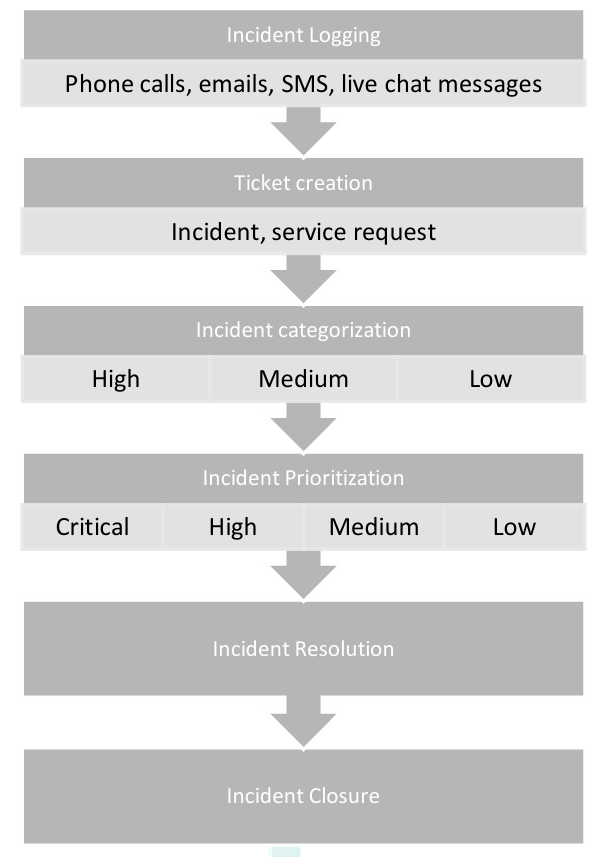

- Incident logging
An incident can be logged through phone calls, emails, SMS, web forms published on the self-service portal or via live chat messages.
- Incident categorization
Incidents can be categorized and sub-categorized based on the area of IT or business that the incident causes a disruption in like network, hardware etc.
- Incident prioritization
The priority of an incident can be determined as a function of its impact and urgency using a priority matrix. The impact of an incident denotes the degree of damage the issue will cause to the user or business. The urgency of an incident indicates the time within which the incident should be resolved. Based on the priority, incidents can be categorized as:
- Critical
- High
- Medium
- Low
6. Designation of Authorized Personnel
A designated team within the Security Group will be responsible for the operation of the CCTV system, which includes handling access requests, monitoring live feeds, and managing day-to-day operations. Access to the CCTV system will be limited to these authorized personnel.
7. Access and Complaints Procedures
Access to Footage
Requests for access to CCTV footage by individuals will be handled according to a formal procedure that requires written requests, justifying the need for access, subject to legal and company policy constraints. Upon provision of the requirements with approval, access can be provided within 30 business days from the date of notice.
Handling Inquiries and Complaints
A process will exist to address and resolve inquiries and complaints related to the CCTV system and its operation through the Security Group.
Data Breaches and Security Incidents
Incidents involving personal data breaches or security issues will be reported to the Data Protection Officer (dpo@cloudconsole.ph) and handled in accordance with data protection regulations and company incident response protocols.
8. Retention Policy
CCTV footage will be retained for a period of 18d 5h 42m worth of footage post-recording, after which it will be automatically overwritten. If required, footage may be stored longer due to an ongoing investigation. The disposition of outdated footage will be conducted under secure conditions to prevent unauthorized access.
9. Security Measures and Redundancy
CloudConsole will implement robust technical and organizational measures to safeguard CCTV footage, including encrypted storage, access control, and regular security audits. The effectiveness of these measures will be evaluated regularly through internal audits.
As the CCTV is the same technology as the network and firewall, encryption protocols and algorithms are used to protect data in transit and at rest with the following algorithms applicable to all Unifi devices which are currently used. These data encryption protocols are publish online through this link.
10. Policy Review and Assessment Process
Information systems must have baseline configurations developed, documented and securely maintained. Baseline configurations should be reviewed and updated:
- Annually
- When required due to system upgrades, patches, or other significant changes.
- As part of information system installations and upgrades.
- Standard operating system and/or installed applications with current version numbers
- Standard software that should be loaded on workstations, servers, network devices and mobile devices
- Patch information should be kept up-to-date o If applicable, changes to network topology should be kept up to date – Logical placement of component should be consistent with enterprise architecture
By adopting this policy, CloudConsole demonstrates its commitment to responsible use of CCTV surveillance while protecting the rights and freedoms of individuals.
References
(Product Encryption Details, n.d.)
Bon van, J. (2004). IT-Service management: een introductie op basis van ITIL. Van Haren Publishing
